Navigating the Risks: Liquidity Mining Pool and Decentralized Applications Scams
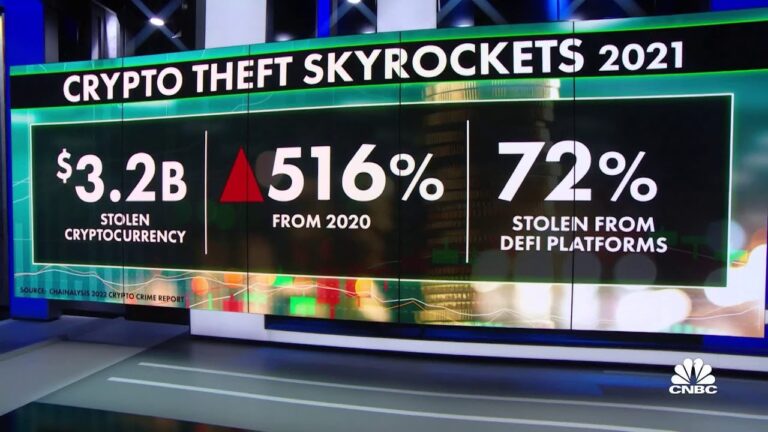
Liquidity Mining Pool and Decentralized Applications Scams: In the expansive world of cryptocurrencies and blockchain technology, innovation and opportunity abound. However, alongside the potential for financial gain, there exists a lurking danger: scams targeting liquidity mining pools and decentralized applications (Dapps). These scams pose a significant risk to both novice and experienced users, making it…